CryptoLocker Virus Removal and Decryption
You’ve probably arrived at this page because your computer is already infected with the cryptolocker virus and just want to know how to remove the virus and decrypt files, in which case skip to the bottom of this article, how do I decrypt and remove the cryptolocker virus
If you need help removing ransomeware or recovering files please contact us, we have a lot of experience working with this virus and its variants.
This article talks specifically about the cryptolocker virus but is relevant to all variants such as cryptowall, CTB-Locker and FileLocker.
Computers are relied upon by businesses for everyday tasks and storing important data. It is therefore important to keep your computer secure from attack by viruses, malware, spyware, hacking and other threats. Keeping a computer secure from the vast majority of attacks (including cryptolocker) is a relatively easy task if you know what you’re doing. As with most things in life, prevention is better than cure and this is very true in the case of the cryptolocker virus.
What is Cryptolocker?
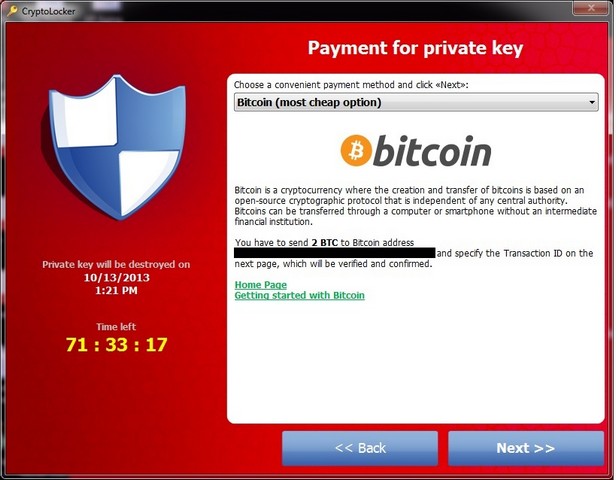
Cryptolocker, is a ransomware Trojan program that has been specially created to target all editions of windows computers (windows XP to Windows 10). It encrypts files on the computer using a RSA and AES-265 encryption, making the files unreadable. The virus also leaves a ‘Read me’ text file with all the encrypted files saying that the only way to unencrypt the files and make them readable again is to pay a ransom of $500 or more. Once the ransom has been paid a digital key is sent that will allow the files to be unlocked. There is also often a dead line of 96 hours for payment or the files will be deleted.
Do NOT pay the ransom
You will not get a decryption key – You are rewarding criminals
How does a computer get infected with the cryptolocker virus?
Unknown websites should always be avoided as they are the most likely means of distributing the virus. Even safe trustworthy websites can be a risk, as they may have been hacked and could infect your PC using specialist exploit kits.
Spam email with attachments, or even links back to the malicious websites is another way of distributing the virus. Often, the email will appear to be from a legitimate source such as FedEx, or DHL. In the email, they may say they tried to deliver a parcel only to find that you weren’t home. It may display a message such as ‘click here to arrange a re-delivery’ and once the link has been clicked, or an attachment has been opened the Cryptolocker virus is initiated.
Downloads that may appear to be genuine, for example, you may think you’re simply downloading and installing an update for software, when in reality, you’re infecting your PC.
Should you pay these fees? – In a word, NO. The people behind this form of encryption are criminals, and paying them will only encourage them to continue their operation and target vulnerable people. It’s also very doubtful that they will send the digital key required to unlock the files.
How do I remove the Cryptolocker Virus?
Due to the larger number of variants of this virus it can prove difficult to clean and if the option is available it is best to completely wipe your Windows computer, reinstall and restore files before the infection happened.
Wiping and restarting isn’t always practical, especially for businesses, in which case you need to do the following.
1 – Find out exactly what variant of the virus you have. This can usually be determined running an antivirus scan which will display the variant if know. If you’re lucky the antivirus software you’re using might actually be able to remove the virus.If the virus scanner returns a generic name then you might need to run a virus scan from a different developer.
2 – Once you know the virus variant do a google search for something like ‘Remove <virus variant name>’ or ‘clean <virus variant name>’
3a – Automatic removal – Depending on the variant you might find a particular antivirus program or removal tool that can automatically remove the virus. Run the tool or scan multiple times until the computer is clean.
3b – Manual removal – If there isn’t an automated method there is often a manual process. Manual process can be very technical and require you to access critical Window’s system files which have the potential to cause more problems.
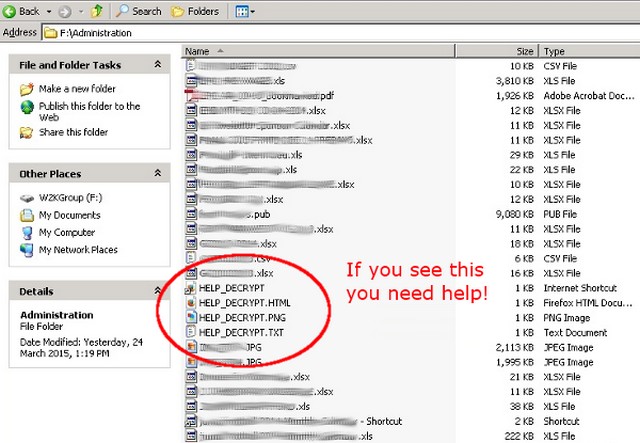
How do i decrypt infected files?
Unfortunately there is currently no way of decrypting the files once infected.
Below are some possible options for file recovery
Important – Before recovering files make sure you understand how the infection occurred in the first place and you have taken action to prevent it happening again.
- Many Windows servers have a feature called ‘Previous version’ this takes a regular snap shot of all files allowing you to go back to a point in time before the infection. If enabled this if by the easiest method of recovering file
- Some versions of Windows computers have recovery versions that allow you to revert back you entire windows computer to the point the last backup was taken
- If you use file sync software such as Dropbox, Onedrive etc. to store your files you can usually go back in file history and restore files before the infection
- For some files it may possible to use data recovery or undelete software to recovery old deleted files
- If you take regular backups using cloud backup software or a local back program simply restore file from before the date of infections.
- Sometime a software developer creates a tool that can resolve previously unresolvable virus issues, such as unencrypting files. For this reason if you have files that you can’t restore from any other method take a full backup of your computer and hope that a solution is developed in the future that can unencrypt your files.
How can i protect my computer from Cryptolocker infection?
There are a number of things you can do to protect computer from threats, with some of the most effective methods being:
- Never open emails from un-trusted sources
- Never visit questionable websites
- Never download files that you aren’t sure about
- Install antivirus and anti-malware
- Cryptolocker can only infect files that a user has permission to access, so always apply the lowest NTFS permission level to user accounts to minimise infection
- Always make sure you have a reliable backup of your data
{fastsocialshare}